From the subscriber’s perspective
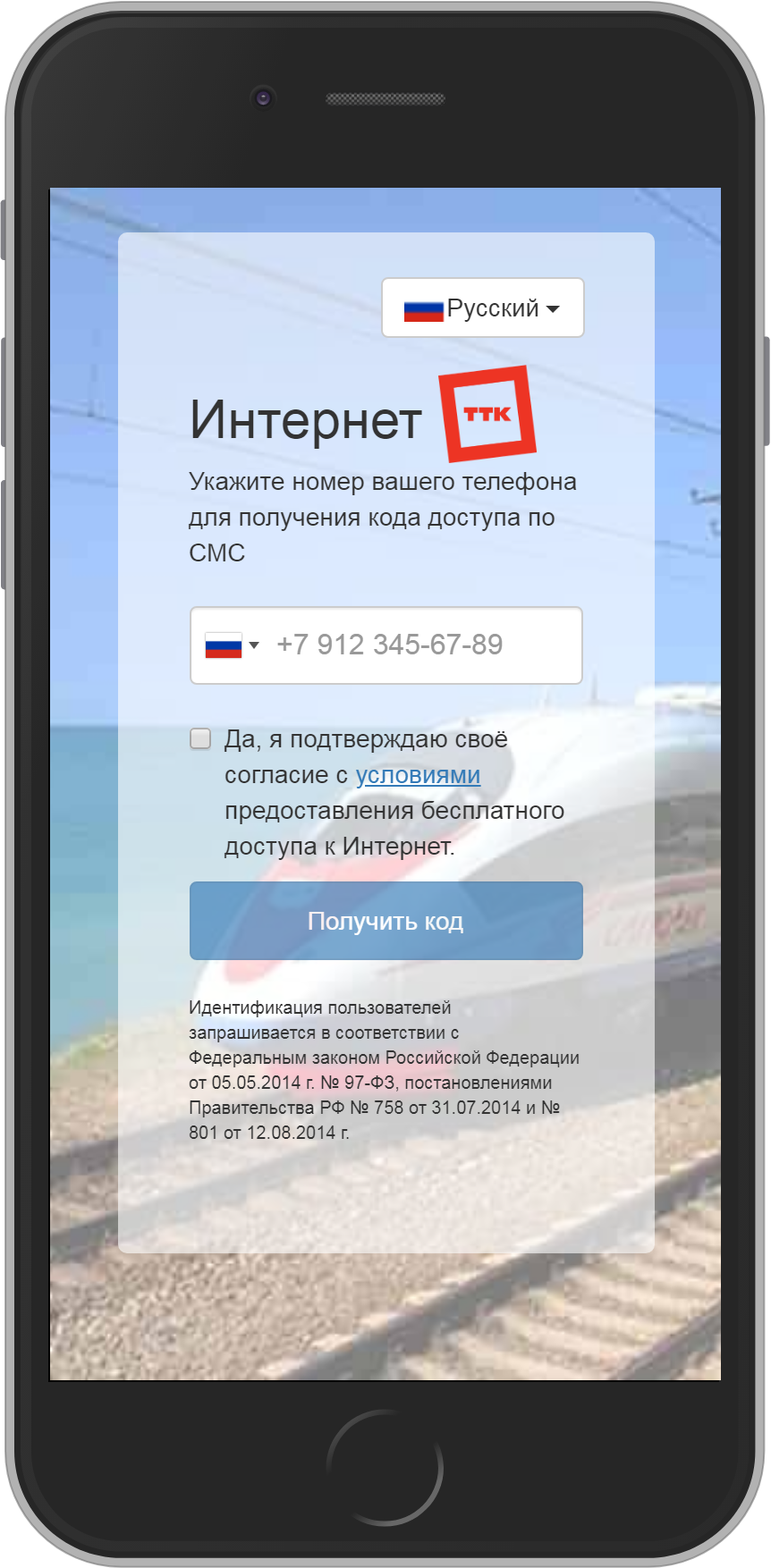
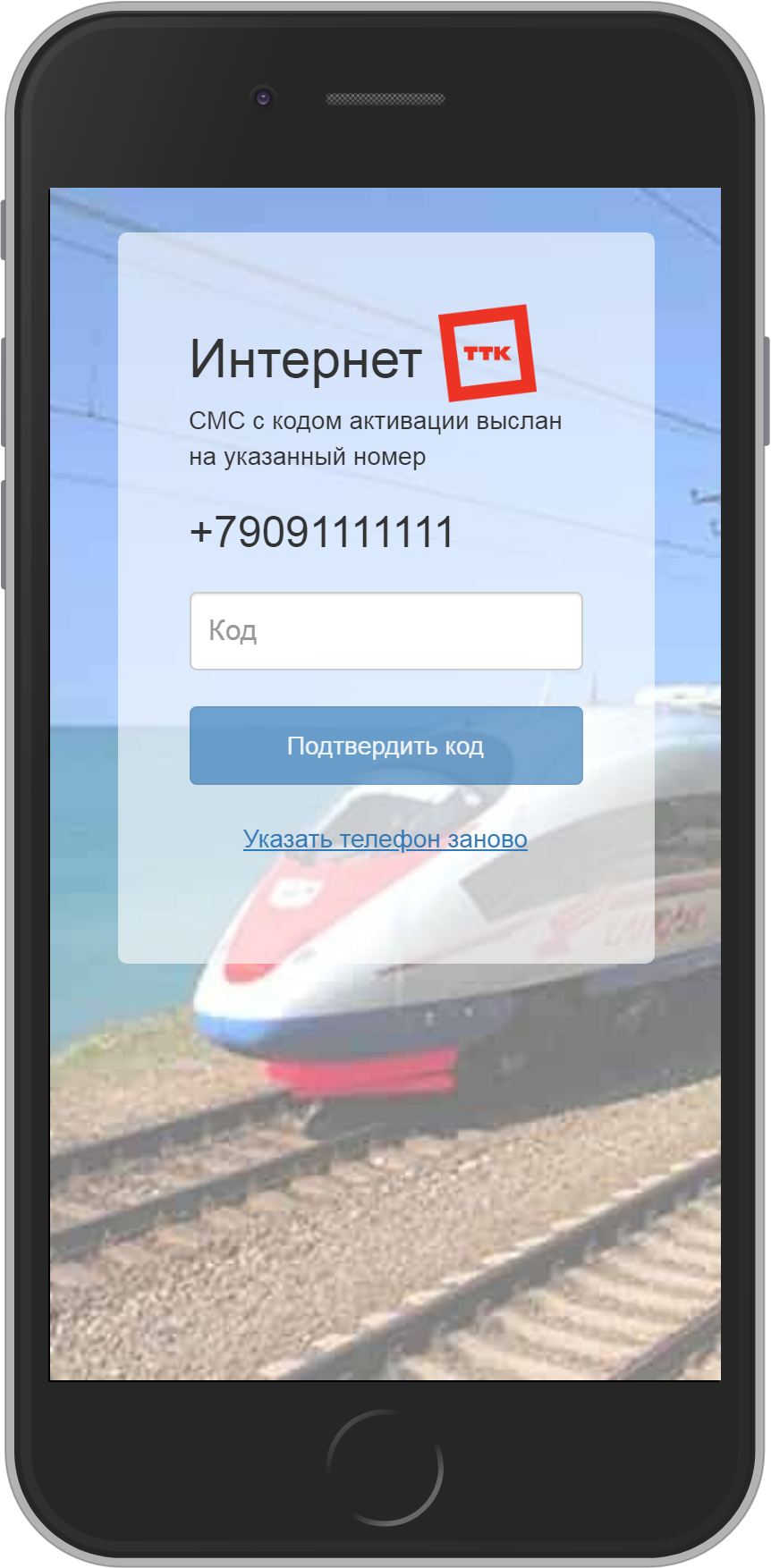
First-time Wi-Fi subscriber connection to a wireless network must be authorized in accordance to the legislative requirements. Most frequently it is done by supplying a mobile phone number and receiving an access code via SMS. It is also possible to make verification by sending an SMS, receiving an incoming or making an outgoing call. A voucher with a unique code given to a subscriber can be applied as well. WNAM offers an opportunity to use the account of Government services portal , the Active Directory account, the fact of registration in the hotel system, and the identification through an external system (for example, by a Russian Railways ticket or accreditation badge number at a public event).
After the initial identification (authorization), and on every subsequent connection, the subscriber will see the welcome page, watch ads, be redirected to the specified website, or connect automatically without additional pop-up windows. A subscriber can be offered to log in through the social network profile (as a supplementary identification), get through a survey, read and accept the usage terms for the current Wi-Fi network, enter an email address or his last name.
Identification (authorization) pages and greetings are available to a subscriber in several languages. In the event of connection error, certain limit exhaustion or equipment malfunction, a subscriber will receive a customizable information message.
From the WI-FI network owner`s perspective
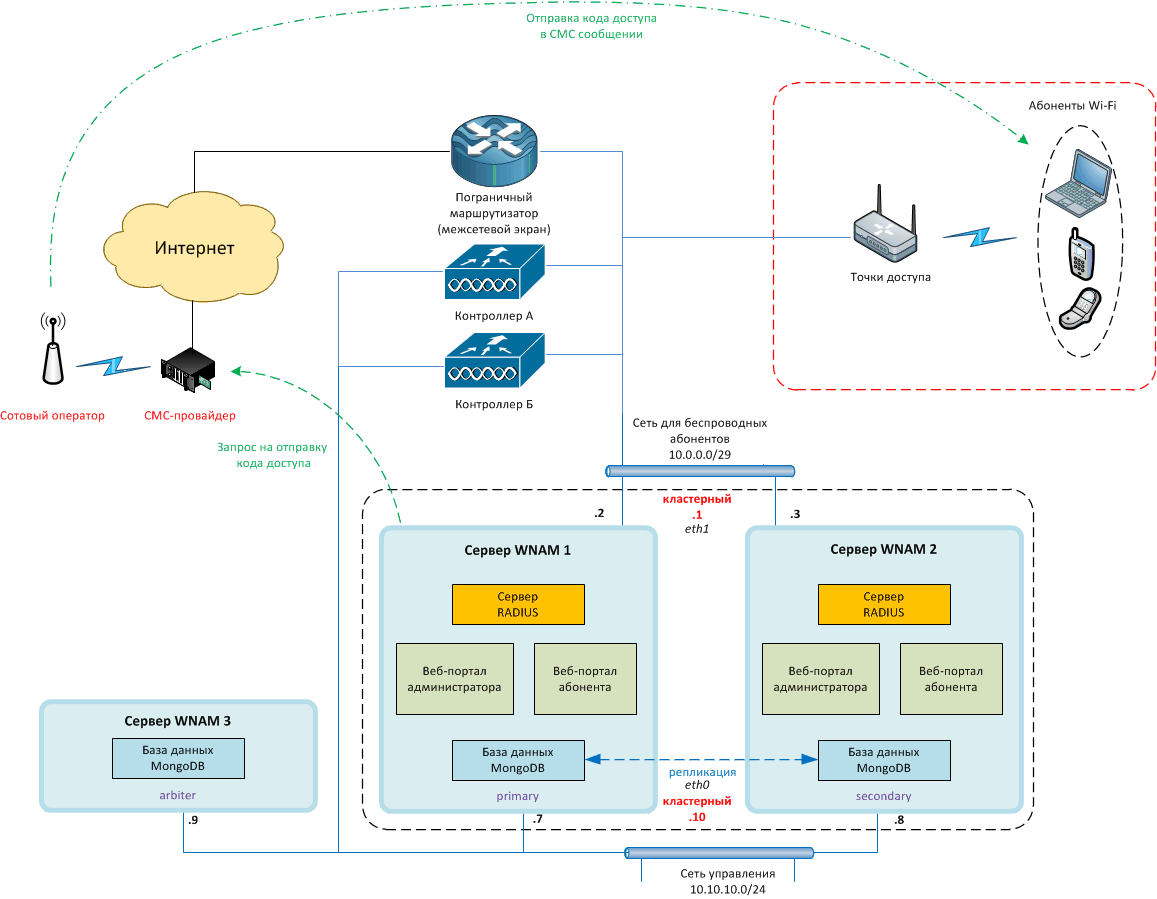
To implement guest authorization service in wireless networks, you need to install a server for the operation of both WNAM software and related services . It can be either a physical server, or a virtual machine. The server has Internet access, and connection to your wireless equipment.
For majority of implementation scenarios the following workflows are applied:
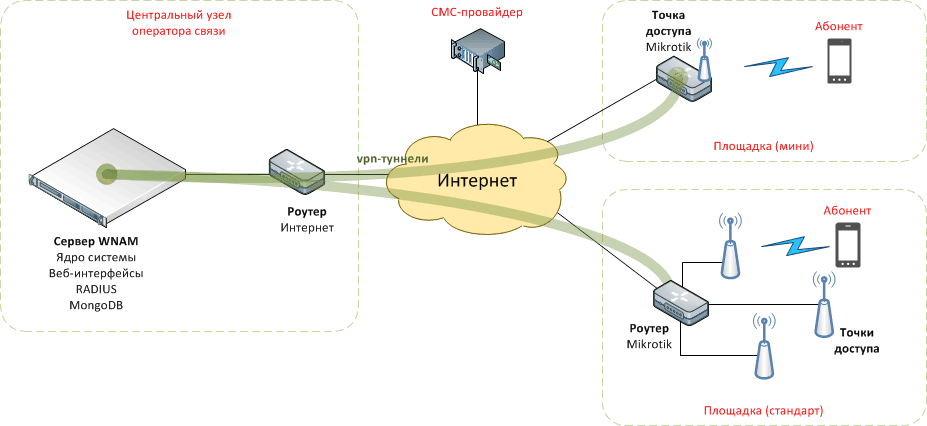
1. Support of a significant number of Wi-Fi locations equipped with an Mikrotik router with a built-in access point, or several access points behind the Mikrotik router. The latter function as a hotspot (captive portal) and provides the interaction of wireless subscribers with WNAM authorization server. For convenient administration, each router is connected to the central node of your network by VPN. That scheme is shown in the picture, and it is popular with most of our customers – regional telecom operators that provide Wi-Fi authentication service to their local customers.
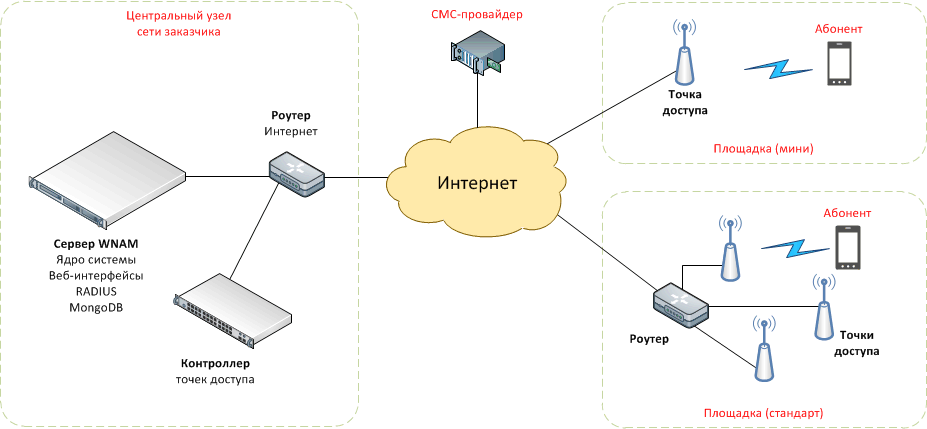
2. The Wi-Fi network controlled by a wireless access point controller. Each location is supplied with one or more access points connected to the controller via the Internet, or a corporate network. It is possible to set up hundreds of access points at only one location (stadium, congress center). In this scheme, the controller performs the functions of a hotspot (captive portal) and enables the interaction of wireless subscribers with WNAM authorization server. The scheme is displayed below, and mainly chosen by corporate customers deploying guest networks with authorization on their own territory.
Any open Wi-Fi network, built of any compatible hardware serves as a foundation for guest access. Dependently on the type of equipment, and wall thickness in the location, each access point produces a reliable service based on radio signal level in a radius of about 15-30 meters. For crowded places with an expected high radio traffic caused by a significant (share of a hundred) number of subscribers per access point, only professional Wi-Fi equipment is suitable.
Subscriber access control is carried out by the Captive Portal. The Captive portal is a specific software component of network equipment (router or access point controller) which ensures the process of redirection of a subscriber’s HTTP request to another (external) server. Upon the connection to an “open” wireless network, most mobile devices identify the Captive portal presence in the network, open a specified “mini-browser” window , which then leads to a unique “subscriber” section of the WNAM web interface, where identification and authorization is done. Consequently, the subscriber is provided with the Internet access followed redirection to the site he had previously intended to visit, or to another webpage (your corporate site, advertisement, etc.).
Our system integrates with the following types of equipment:
- Cisco WLCs (controllers) and appropriate access points
- Bluesocket controllers and appropriate access points
- Aruba controllers and access appropriate points
- Ruckus ZoneDirector, SmartZone, Virtual SmartZone, SmartCell Gateway controllers and appropriate access points
- Zyxel NXC, UAG controllers and appropriate access points
- Ubiquiti UniFi controllers and appropriate access points
- Motorola / Zebra / Extreme controllers with WiNG software
- Mikrotik routers with support for RouterOS Level> 4
- Routers based on pfSense firmware
- BRAS devices based on Cisco SSG and ISG (ASR, 7200, 10K)
- Linux server-based routers
- Alcatel-Lucent SR Routers
- TP-LINK EAP or CAP controllers appropriate and access points
- Hewlett-Packard Enterprises (HPE) MSM controllers and appropriate access points
- Huawei AC controllers with points in Fit mode, and standalone AP points in Fat mode
- Eltex access points such as WEP or WOP
- Access points Rotek
- Keenetic Access Points
- Cambium Networks Access Points
- DCN controllers and appropriate access points
- Avaya controllers and appropriate access points
- FortiWLC controllers
- Ruijie Networks controllers and appropriate access points
Traditionally the Captive portal is built into the wireless controller or access point, which provides radio access too. Another option is the Captive portal at router (Mikrotik, pfSense, Cisco ISG), while the radio network can be supplied by other equipment, for instance cheap D-Link APs operating in Open network mode.
Network traffic amount collection is performed by RADIUS protocol, supported individually for each type of abovementioned equipment. WNAM also determines and records the type, manufacturer, the name of the subscriber’s device (via DHCP identifiers), hotspot, name and addresses of access points, radio channel and signal level as well as other relevant information important in guest profile creation and advertisement targeting.
Subscriber guest accounts are created automatically after successful authorization, and stored in the WNAM database indefinitely. Identity SMS routing can be possible via SMS aggregators (SMSC.ru, smstraffic.ru, WebSms.by), a locally connected GSM modem (gammu), connection to an SMS distribution provider using the standard SMPP protocol (Kannel gateway) , via HTTP GET / POST API or through a script. To reduce SMS sending expenses it is possible to follow an alternative approach, when the subscriber himself sends an SMS to your system at his own expense. Call identification option can be employed as well: the subscriber receives an incoming call with the pronounced access code, or a subscriber himself makes a phone call to number terminated at your Asterisk gateway. The authorization via Active Directory, vouchers, the State Service Portal (ESIA), and through any external system via API is fully supported.
Detailed statistics on visited Internet resources is collected as traffic flows according to the Netflow v5 or v9 data exported by your router (no visited URL resources visibility).
With the Captive portal a redirection of the subscriber`s web session to an external URL or to advertisement page is possible (regardless of authorization type). For this purpose WNAM has flexible advertising tools. There is also a built-in online editor for authorization page templates, styles, advertisement content, the option of logo and styles uploading, etc. The editor provides simple (visual) and expert (HTML code level) operating modes. All WNAM settings are done via the web interface:
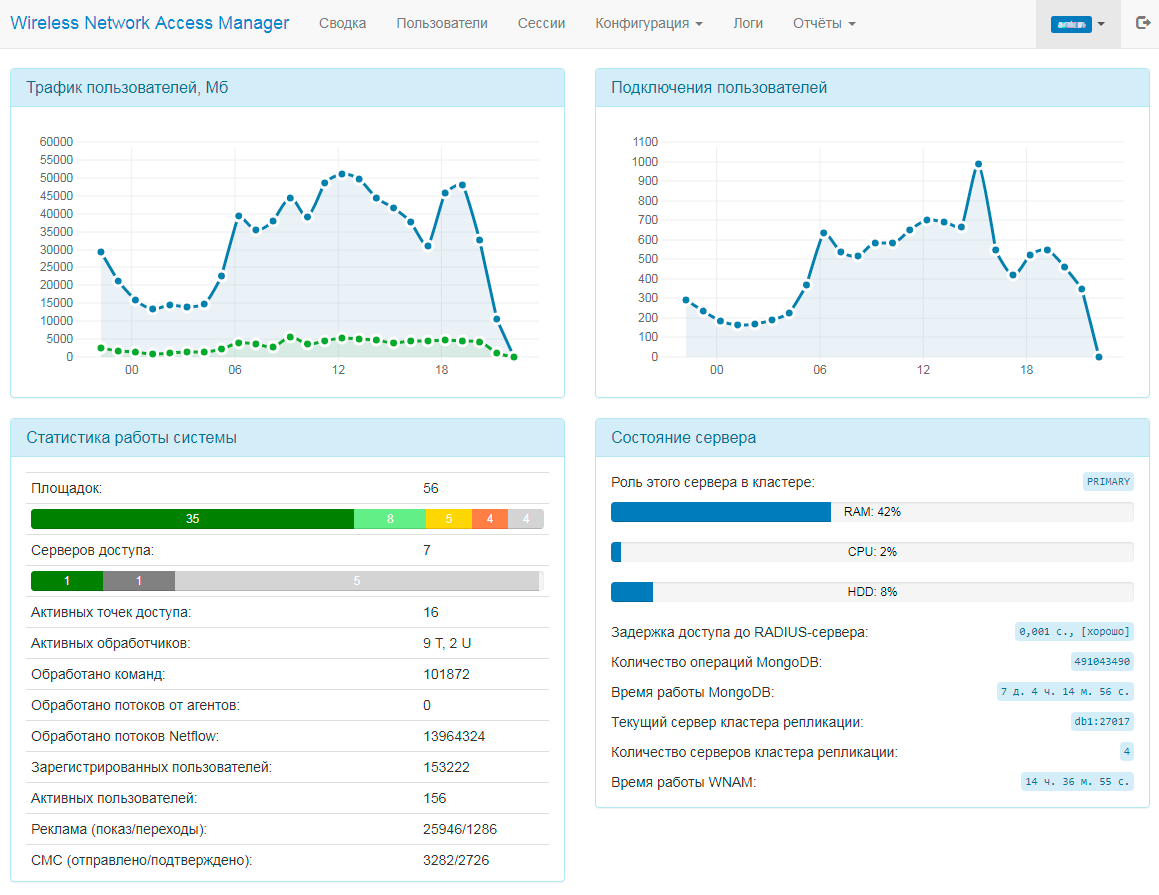
WNAM allows you to create various types of reports with uploading to CSV, PDF and Excel formats, for example:
- On traffic, subscriber, sessions, ranged by time
- On traffic, subscriber, sessions, ranged by access locations
- On the traffic volume distribution in a subscriber session
- Selected subscriber time and location statistics
- Which subscribers were active at location at a given period of time, which of them visited a given resource or accessed an external IP address
- Viewed and clicked advertisement blocks and campaigns
- Identity SMS sending, delivery and confirmation, subscribers’ phone numbers.
A set of reports can be modified by your request.
WNAM is installed on a Linux server (physical or virtual) scaled in accordance to planned number of simultaneous subscribers of your Wi-Fi network. Typical server parameters are: 2-4 vCPU, 8 Gb vRAM, 200 Gb vHDD. You can install and configure the WNAM system yourself using the open documentation, or entrust this work to our experts for a small fee.
For large networks with increased reliability requirements, a cluster system configuration (three to six WNAM servers) with a replicated database can be deployed.